


> Proactively monitor 1,000s of threat indicators in real time
> Block known threats that get beyond the endpoint protection
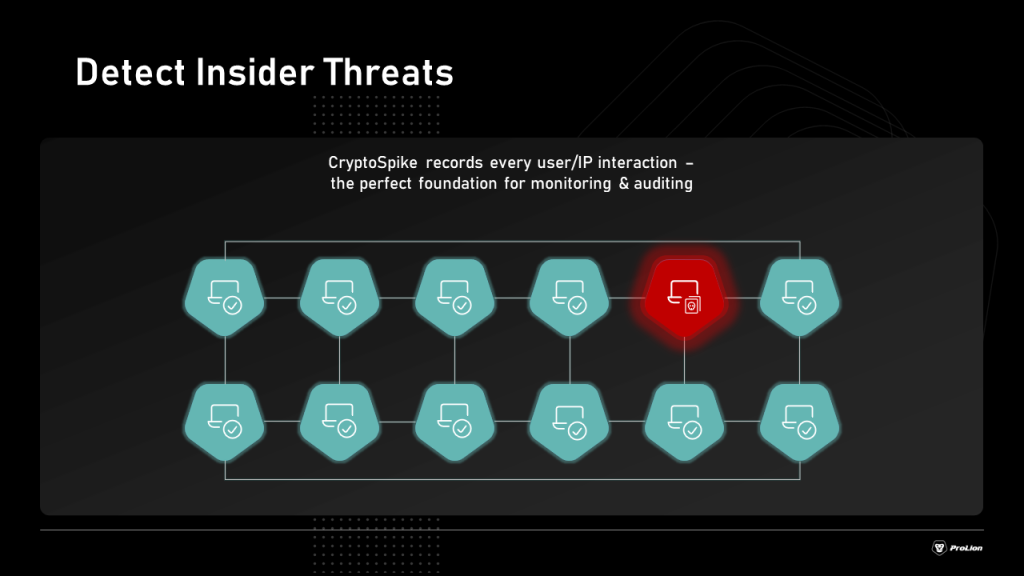
> Full data visibility with traceability of access at the file level
> Restore only what you need to restore down to a single file via snapshots
> Integrate into the existing SIEM platform
> Deploy within one to two hours, on-premises or in the cloud
> Ability to customize monitoring policies by volume or department level

השאירו פרטים ונחזור אליכם בהקדם:
WhatsApp us